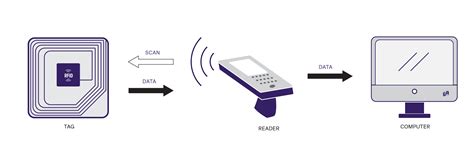
rfid surveillance chips A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . $67.50
0 · what is rfid technology
1 · what is rfid security
2 · what is rfid card
3 · what is rfid bar code
4 · microchips in cyber security
5 · microchips for human use
6 · microchips challenges
7 · are rfid tags safe
Jual Beli Nfc Reader Android Online Terlengkap, Aman & Nyaman di .
what is rfid technology
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See more
Some people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See more
RFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain .
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.If you’re interested in the NXP ICODE® chip series or looking for RFID solutions, this article is a must-read reference. This guide will dive deep into the key features, common application scenarios, and unique advantages of the NXP ICODE® chip series, showing how it can help industries around the globe improve operational efficiency and enhance security by providing . Microchips in humans: consumer-friendly app, or new frontier in surveillance? By Ahmed Banafa | September 8, 2022 An x-ray showing a Walletmor RFID chip injected into a person’s hand after a local anesthetic.
what is rfid security
RFID technology uses small chips to store and transmit information wirelessly for tracking and identification purposes. Learn all about RFID. RFID chips use radio signals to transmit data over short distances. They are used typically for security, tracking, monitoring and identification purposes. RFID chips can be paired with other circuitry to create tags or readers that also use .RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
There are many types of RFID chips from many manufacturers such as NXP, HID, EM, and Legic. You can find these chips in many applications such as public transport cards, credit cards, university cards, supply chain trackers, etc. Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming" the.While intended to deter fraud and improve security, RFID chips introduce other fears. Here's how. RFID, or radio frequency identification, is wireless technology that uses electromagnetic frequencies to uniquely identify a person, object or animal. RFID is comparable to barcode technology, but there are key differences. RFID tags do not require .
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.If you’re interested in the NXP ICODE® chip series or looking for RFID solutions, this article is a must-read reference. This guide will dive deep into the key features, common application scenarios, and unique advantages of the NXP ICODE® chip series, showing how it can help industries around the globe improve operational efficiency and enhance security by providing . Microchips in humans: consumer-friendly app, or new frontier in surveillance? By Ahmed Banafa | September 8, 2022 An x-ray showing a Walletmor RFID chip injected into a person’s hand after a local anesthetic.
RFID technology uses small chips to store and transmit information wirelessly for tracking and identification purposes. Learn all about RFID. RFID chips use radio signals to transmit data over short distances. They are used typically for security, tracking, monitoring and identification purposes. RFID chips can be paired with other circuitry to create tags or readers that also use .
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. There are many types of RFID chips from many manufacturers such as NXP, HID, EM, and Legic. You can find these chips in many applications such as public transport cards, credit cards, university cards, supply chain trackers, etc.
Passports and some credit cards have RFID chips that allow information to be read wirelessly. An industry has sprung up to make wallets and other products that block hackers from "skimming" the.
what is rfid card
what is rfid bar code
oyster card contactless payment
Week 11 Schedule. View the full Week 11 broadcast schedule on SiriusXM and find out more about some of the most-anticipated upcoming matchups:. November 9 at 12pm ET: Miami vs. Georgia Tech November 9 at .
rfid surveillance chips|what is rfid security