how serious is rfid card hacking June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be .
ANALYST. John Parker Wilson, was a three-year Quarterback starter for the Crimson Tide from 2006-08. He spent five years in the NFL with the Falcons, Jaguars and Steelers. Wilson finished his Tide career as the school’s all-time .Fly By Radio band specializes in college parties, corporate events, and weddings. With over two thousand events played, Fly By Radio has the experience to make sure your .
0 · rfid scam
1 · problems with rfid technology
2 · problems with rfid
3 · is rfid safe to hack
4 · is rfid dangerous
5 · how to stop rfid scanning
6 · how to prevent rfid cloning
7 · how to block rfid scanning
List via AuburnTigers.com of radio stations across the South that air Auburn football games.. Auburn Football Radio Affiliates {}Abbeville WESZ-FM 98.7 {}Greenville .
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos by blocking access with ID cards.Despite its many benefits, RFID technology is vulnerable to hacking in several ways. First, RFID signals can be intercepted, allowing an attacker to eavesdrop on sensitive data. Second, attackers can use a high-powered reader to .
tracking rfid stickers
RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos . One of the biggest public fears surrounding RFID hacking is with credit and debit cards. While your RFID card is safe in your wallet, a hacker scans the card in your pocket .Despite its many benefits, RFID technology is vulnerable to hacking in several ways. First, RFID signals can be intercepted, allowing an attacker to eavesdrop on sensitive data. Second, .
June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be .
hotel rfid lock system
The majority of attacks against RFID systems can be broken into three major categories: man-in-the-middle (MITM), cloning, and brute forcing. Man-in-the-Middle. An attack .Furthermore, RFID hacking can have serious implications in industries where safety and security are paramount. For example, in the transportation sector, attackers could exploit vulnerabilities . Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal . If you use RFID-enabled devices such as key fobs, access cards, or even vehicle transponders, consider protecting them from hacking attempts. You can do this by using .
passive rfid asset tracking system
Hackers can and have jammed RFID cards and tags from working simply by being nearby and generating a signal that is stronger than the one being put out by the RFID reader. .
RFID systems, like most electronics and networks, are susceptible to both physical and electronic attacks. As the technology matures and becomes more widespread, so do . RFID cards and tags can be rendered useless by hackers who generate a stronger signal than the RFID reader. This not only disrupts inventory tracking but also causes chaos . One of the biggest public fears surrounding RFID hacking is with credit and debit cards. While your RFID card is safe in your wallet, a hacker scans the card in your pocket .Despite its many benefits, RFID technology is vulnerable to hacking in several ways. First, RFID signals can be intercepted, allowing an attacker to eavesdrop on sensitive data. Second, .
June 9, 2022. Summary: Products such as “RFID wallets” claim to prevent frauds and scams like RFID skimming, in which thieves steal information off your chip-embedded credit card. Be .
The majority of attacks against RFID systems can be broken into three major categories: man-in-the-middle (MITM), cloning, and brute forcing. Man-in-the-Middle. An attack .

Furthermore, RFID hacking can have serious implications in industries where safety and security are paramount. For example, in the transportation sector, attackers could exploit vulnerabilities . Security Risks. RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal .
rfid scam
problems with rfid technology
If you use RFID-enabled devices such as key fobs, access cards, or even vehicle transponders, consider protecting them from hacking attempts. You can do this by using . Hackers can and have jammed RFID cards and tags from working simply by being nearby and generating a signal that is stronger than the one being put out by the RFID reader. .
problems with rfid
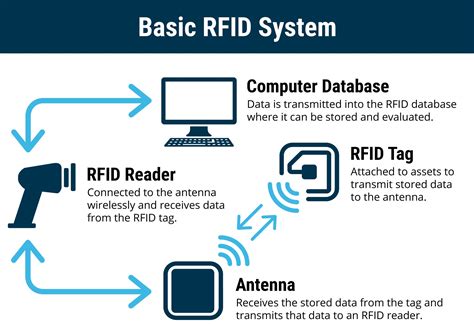
silent sensors rfid
wireless rfid temperature sensors
The affiliation with the Auburn Sports Network across programming on multiple local radio stations promises an unmatched experience for passionate Auburn sports fans. Wings 94.3 will air Auburn football games, men’s .
how serious is rfid card hacking|problems with rfid technology