virtual smart card no tpm Microsoft offeres "Virtual Smartcards" that use the TPM. I should be able to access them via PKCS11 from the OpenVPN client.config. There are CAPI to PKCS11 . USB NFC Smart IC Card Reader Writer Copier Duplicator Contactless 13.56MHz 424kbps .
0 · virtual tpm windows 10
1 · virtual smart card windows 11
2 · virtual smart card windows 10
3 · tpmvscmgr list virtual smart cards
4 · smart card resource manager download
5 · smart card eim login
6 · smart card authentication step by
7 · install microsoft smart card manager
This document contains the release information for the NXP NFC Reader Library for the reader frontend ICs namely PN5180, PN5190, CLRC663 and NFC controller PN7462AU. The Source .This multi-layer library, written in C, makes it easy to create NFC based applications. Special .
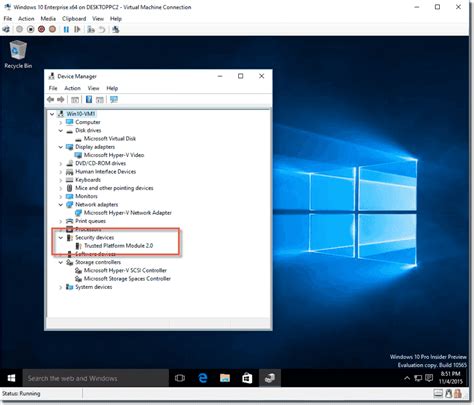
Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of .
If the TPM is disabled in the BIOS, or it isn't provisioned with full ownership and the storage root key, the TPM virtual smart card creation fails; If the TPM is initialized after . This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new .
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI .
Microsoft offeres "Virtual Smartcards" that use the TPM. I should be able to access them via PKCS11 from the OpenVPN client.config. There are CAPI to PKCS11 .To create and delete TPM virtual smart cards for end users, the Tpmvscmgr command-line tool is included as a command-line tool with the operating system. You can use the Create and .I don't understand Microsoft's (Virtual) Smart Cards. : r/cybersecurity. I get that the 'something you have' factor in MFA generally has to be represented by data. It's not actually the physical . The virtual smart card platform is limited to the use of the Trusted Platform Module (TPM) chip, which is on most modern devices. Virtual smart cards that utilize a TPM provide .
Virtual Smart Cards function very similarly to conventional Smart Cards. The difference is the private key is protected by the TPM and not the smart card media. The Virtual . By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices.
virtual tpm windows 10
virtual smart card windows 11
unique features of smart cards
If the TPM is disabled in the BIOS, or it isn't provisioned with full ownership and the storage root key, the TPM virtual smart card creation fails; If the TPM is initialized after creating a virtual smart card, the card will no longer function, and it must be re-created This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM). Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps:
To create and delete TPM virtual smart cards for end users, the Tpmvscmgr command-line tool is included as a command-line tool with the operating system. You can use the Create and Delete parameters to manage virtual smart cards on local or remote computers. For information about using this tool, see Tpmvscmgr. I don't understand Microsoft's (Virtual) Smart Cards. : r/cybersecurity. I get that the 'something you have' factor in MFA generally has to be represented by data. It's not actually the physical presence of the token. The virtual smart card platform is limited to the use of the Trusted Platform Module (TPM) chip, which is on most modern devices. Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering.
Virtual Smart Cards function very similarly to conventional Smart Cards. The difference is the private key is protected by the TPM and not the smart card media. The Virtual smart card emulates a smart card and reader so the device presents itself to operating system and applications as a traditional smart card. Trying to have a good overview about the security of Virtual Smart Cards relying on TPMs, I read this very short article (the only I found) covering this topic (first part): https://docs.microsoft.com/en-us/windows/security/identity-protection/virtual-smart-cards/virtual-smart-card-evaluate-security. My understanding.
By utilizing Trusted Platform Module (TPM) devices that provide the same cryptographic capabilities as physical smart cards, virtual smart cards accomplish the three key properties that are desired by smart cards: nonexportability, isolated cryptography, and .
Virtual smart card technology offers comparable security benefits to physical smart cards by using two-factor authentication. Virtual smart cards emulate the functionality of physical smart cards, but they use the Trusted Platform Module (TPM) chip that is available on devices. If the TPM is disabled in the BIOS, or it isn't provisioned with full ownership and the storage root key, the TPM virtual smart card creation fails; If the TPM is initialized after creating a virtual smart card, the card will no longer function, and it must be re-created This is my first blog and today I’ll share with you how to configure a Hyper-V environment in order to enable virtual smart card logon to VM guests by leveraging a new Windows 10 feature: virtual Trusted Platform Module (TPM).
Virtual smart cards can be used in domain-joined Windows 10 devices equipped with a TPM (version 1.2 or version 2.0). In addition, they require an accessible PKI infrastructure in the environment, such as Microsoft Certificate Services. The basic process of using virtual smart cards involves three steps:To create and delete TPM virtual smart cards for end users, the Tpmvscmgr command-line tool is included as a command-line tool with the operating system. You can use the Create and Delete parameters to manage virtual smart cards on local or remote computers. For information about using this tool, see Tpmvscmgr. I don't understand Microsoft's (Virtual) Smart Cards. : r/cybersecurity. I get that the 'something you have' factor in MFA generally has to be represented by data. It's not actually the physical presence of the token. The virtual smart card platform is limited to the use of the Trusted Platform Module (TPM) chip, which is on most modern devices. Virtual smart cards that utilize a TPM provide the three main security principles of traditional smart cards: nonexportability, isolated cryptography, and anti-hammering.
Virtual Smart Cards function very similarly to conventional Smart Cards. The difference is the private key is protected by the TPM and not the smart card media. The Virtual smart card emulates a smart card and reader so the device presents itself to operating system and applications as a traditional smart card.
types smart card ppt
virtual smart card windows 10
MenuItem; import android.nfc.*; import android.nfc.tech.*; import android.nfc.NfcAdapter.ReaderCallback; import android.content.Intent; import .A Library to read e-money card number and balance. Contribute to zero3003/read_card_nfc .
virtual smart card no tpm|tpmvscmgr list virtual smart cards