smart card public private key In context of smart cards, the certificate(s) gets copied (propagated to) trust stores on insertion, but the private key stays on the smart card. This means that the certificate, public and private key is stored on the smart card, but that the certificate (and public key) is free to leave. From high-quality character figures to super-portable cards, amiibo can come in different shapes and sizes. You can tap your amiibo to the right Joy-Con™ controller's Right Stick or the NFC .
0 · public key cryptography
1 · public key authentication examples
2 · public key authentication
3 · certificate based public key authentication
1. Popl. First on the list is Popl, one of the top NFC business card apps available online. Popl is a digital business card platform for both teams and individuals that allows you to instantly share your information when .
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for . In context of smart cards, the certificate(s) gets copied (propagated to) trust stores on insertion, but the private key stays on the smart card. This means that the certificate, public and private key is stored on the smart card, but that the certificate (and public key) is free to leave.
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.
nfl current wild card standings
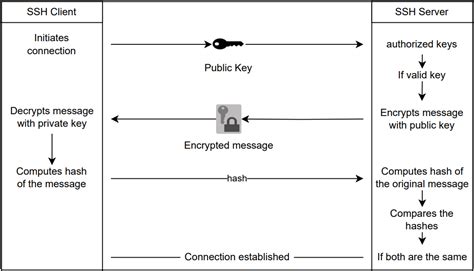
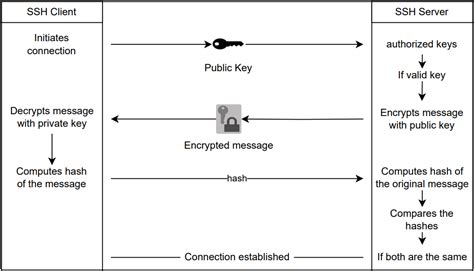
The idea is simple: Public Key Authentication for SSH is well documented, I just want my private key to live on my hardware token instead of being a file on my hard drive. Interactive sign-in in Windows begins when the user presses CTRL+ALT+DEL. The CTRL+ALT+DEL key combination is called a secure attention sequence (SAS). To keep other programs and processes from using it, Winlogon registers this .One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.In the case of smart card authentication, your user credentials, that is your public and private keys and certificate, are stored on a smart card and can only be used after the smart card is inserted into the reader and a PIN is provided.
What benefits do smart cards capable of storing private keys, and devices like the YubiKey Neo (which seems to be a smart card + usb reader in a single dongle) offer above storing private keys on a plain-old usb thumb drive? Does the smart card ever "reveal" the private key to applications like SSH or GPG?
public key cryptography
Key based authentication enables the SSH server and client to compare the public key for a user name provided against the private key. If the server-side public key can't be validated against the client-side private key, authentication fails.It needs to be able to extract the public-key from the smartcard, and to do that through the X.509 certificate. yubico-piv-tool -a verify-pin -a selfsign-certificate -s 9a -S "/CN=SSH key/" -i public.pem -o cert.pem. Note. This command will prompt for the PIV PIN. The default PIV PIN is 123456.

The benefits of PKI. Public key infrastructure achieves privacy through an architecture that operates using public/private key pairs (see Table 2 for a more in-depth overview of the key issuance process). Take the simplistic example of ‘person A’ (the message sender) wanting to send a private message to ‘person B’ (the message recipient). In context of smart cards, the certificate(s) gets copied (propagated to) trust stores on insertion, but the private key stays on the smart card. This means that the certificate, public and private key is stored on the smart card, but that the certificate (and public key) is free to leave.
Your PIV/CAC credential contains an authentication certificate key pair (public and private) for smart card logon. Using a PIV/CAC key pair is very similar to using a self-signed key pair for SSH.
The idea is simple: Public Key Authentication for SSH is well documented, I just want my private key to live on my hardware token instead of being a file on my hard drive. Interactive sign-in in Windows begins when the user presses CTRL+ALT+DEL. The CTRL+ALT+DEL key combination is called a secure attention sequence (SAS). To keep other programs and processes from using it, Winlogon registers this .
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server.
In the case of smart card authentication, your user credentials, that is your public and private keys and certificate, are stored on a smart card and can only be used after the smart card is inserted into the reader and a PIN is provided.What benefits do smart cards capable of storing private keys, and devices like the YubiKey Neo (which seems to be a smart card + usb reader in a single dongle) offer above storing private keys on a plain-old usb thumb drive? Does the smart card ever "reveal" the private key to applications like SSH or GPG? Key based authentication enables the SSH server and client to compare the public key for a user name provided against the private key. If the server-side public key can't be validated against the client-side private key, authentication fails.
It needs to be able to extract the public-key from the smartcard, and to do that through the X.509 certificate. yubico-piv-tool -a verify-pin -a selfsign-certificate -s 9a -S "/CN=SSH key/" -i public.pem -o cert.pem. Note. This command will prompt for the PIV PIN. The default PIV PIN is 123456.
nfl projected standings 2023
public key authentication examples
public key authentication
whos in the wild card nfl
certificate based public key authentication
This app was made to read public data on an NFC banking card compliant with EMV norm. Pro .
smart card public private key|public key authentication