smart card authentication tutorial In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login and unlock and also some basic principles that are common to headless setups.
Just listen for your chance to call in and win between 6am and 10pm! Facebook X Copy Link Email Share. Chuck and Chernoff LIVE from Whataburger – Buford! November 13, 2024 2:00 pm. “The Locker Room” LIVE from Handel’s Ice .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games are broadcast across the entire state of Alabama plus portions of .
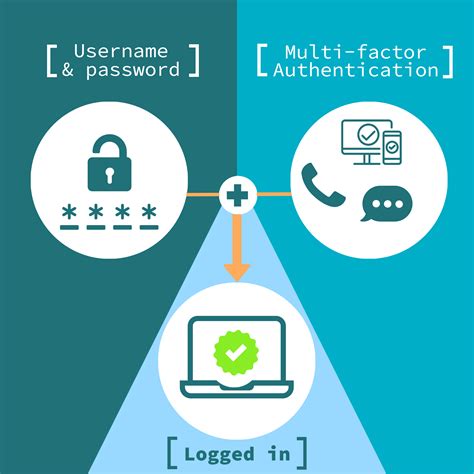
smart card multi factor authentication
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to .
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy.
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Smart Card is a physical electronic authorization device used to control data accessing and data manipulation. It is basically plastic embedded with an integrated circuit. On the smart card, either a memory chip or a microprocessor is fabricated to store the data and connect with the system.
Coolkey is a LDAP server that provides smart card login, single sign-on, secure messaging, and secure email access. Here is a ton of information on how to set up a PKI and ROOT CA that allows for smartcard use.In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login and unlock and also some basic principles that are common to headless setups.To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.1. Understanding smart card authentication. 2. Configuring Identity Management for smart card authentication. 3. Configuring certificates issued by ADCS for smart card authentication in IdM. 4. Certificate mapping rules for configuring authentication. 5. Configuring smart card authentication with the web console for centrally managed users. 6.
smart card identity
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server. One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to . The smart card, a device that is typically a plastic credit-card sized device with an IC chip, contains a X.509 certificate and the corresponding private key for use with authentication.
Virtual smart cards are a technology from Microsoft that offers comparable security benefits in two-factor authentication to physical smart cards. They also offer more convenience for users and lower cost for organizations to deploy.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. Smart Card is a physical electronic authorization device used to control data accessing and data manipulation. It is basically plastic embedded with an integrated circuit. On the smart card, either a memory chip or a microprocessor is fabricated to store the data and connect with the system.
Coolkey is a LDAP server that provides smart card login, single sign-on, secure messaging, and secure email access. Here is a ton of information on how to set up a PKI and ROOT CA that allows for smartcard use.
In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login and unlock and also some basic principles that are common to headless setups.To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.1. Understanding smart card authentication. 2. Configuring Identity Management for smart card authentication. 3. Configuring certificates issued by ADCS for smart card authentication in IdM. 4. Certificate mapping rules for configuring authentication. 5. Configuring smart card authentication with the web console for centrally managed users. 6.
One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to the server. One of the authentication methods supported by the SSH protocol is public key authentication. A public key is copied to the SSH server where it is stored and marked as authorized. The owner of the corresponding private key in the smart card can then SSH login to .
smart card based identification system
smart card authentication step by
smart card status check online cg
You can listen to live Auburn Tigers games online or on the radio dial. With 54 stations in the network, the Auburn Sports Network represents one of the biggest and most-listened to college sports network in the South. All home and away .
smart card authentication tutorial|enable smart card log on