smart cards tokens security and applications pdf download presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.
$9.99
0 · what is smart card number
1 · what is smart card authentication
2 · smart card identity
3 · smart card identification
4 · smart card based identification system
5 · smart card based authentication
6 · memory based smart card
7 · azure smart card authentication
The "NFC Card Emulator" is an application created to test the communication unit between the smart card reader and the smart card. It uses the Host-Based Card Emulation method in the .
Download book PDF. Download book EPUB. Overview. Editors: Keith Mayes, Konstantinos Markantonakis. Revised and updated edition with new content on RFIDs, embedded security, .

small passive rfid readers
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application .presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.Smart Cards, Tokens, Security and Applications provides a broad overview of the many card systems and solutions that are in practical use today. This state-of-the art work is written by .
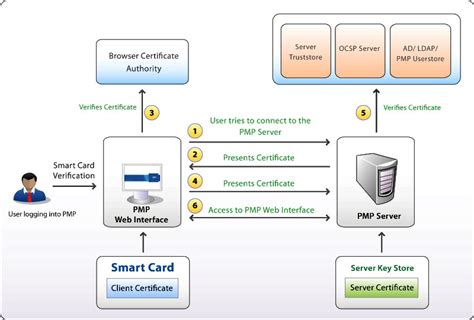
what is smart card number
Smart Cards, Tokens, Security and Applications. This state-of-the art work combines a cross-discipline overview of smart cards, tokens and related security and .presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.
”Smart Cards, Tokens, Security and Applications” by Keith Mayes and Konstantinos Markantonakis (editors), SPRINGER. 2008. ISBN: 978-0-387-72197-2. Eric Diehl Security .This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study. A step-by-step approach educates the reader in card . Request PDF | Smart Cards, Tokens, Security and Applications | This book provides a broad overview of the many card systems and solutions that are in practical use . Smart Cards, Tokens, Security and Applications provides a broad overview of the many card systems and solutions that are in practical use today. This state-of-the art work is .
what is smart card authentication
smart card identity
Download book PDF. Download book EPUB. Overview. Editors: Keith Mayes, Konstantinos Markantonakis. Revised and updated edition with new content on RFIDs, embedded security, .

A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application .
presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.
Smart Cards, Tokens, Security and Applications provides a broad overview of the many card systems and solutions that are in practical use today. This state-of-the art work is written by . Smart Cards, Tokens, Security and Applications. This state-of-the art work combines a cross-discipline overview of smart cards, tokens and related security and .presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.”Smart Cards, Tokens, Security and Applications” by Keith Mayes and Konstantinos Markantonakis (editors), SPRINGER. 2008. ISBN: 978-0-387-72197-2. Eric Diehl Security .
This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study. A step-by-step . Request PDF | Smart Cards, Tokens, Security and Applications | This book provides a broad overview of the many card systems and solutions that are in practical use .
Smart Cards, Tokens, Security and Applications provides a broad overview of the many card systems and solutions that are in practical use today. This state-of-the art work is .Download book PDF. Download book EPUB. Overview. Editors: Keith Mayes, Konstantinos Markantonakis. Revised and updated edition with new content on RFIDs, embedded security, .
A step-by-step approach educates the reader in card types, production, operating systems, commercial applications, new technologies, security design, attacks, application .presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.Smart Cards, Tokens, Security and Applications provides a broad overview of the many card systems and solutions that are in practical use today. This state-of-the art work is written by .
Smart Cards, Tokens, Security and Applications. This state-of-the art work combines a cross-discipline overview of smart cards, tokens and related security and .
smart card identification
presents the main features of smart card technology in the light of the EMV card specifications. The discussion continues with 3D secure and token authentication.”Smart Cards, Tokens, Security and Applications” by Keith Mayes and Konstantinos Markantonakis (editors), SPRINGER. 2008. ISBN: 978-0-387-72197-2. Eric Diehl Security .This book combines a cross-discipline overview of smart cards, tokens and related security and applications plus a technical reference to support further research and study. A step-by-step . Request PDF | Smart Cards, Tokens, Security and Applications | This book provides a broad overview of the many card systems and solutions that are in practical use .
smart card based identification system
Once you create a Blinq account, you will need to verify your email add.
smart cards tokens security and applications pdf download|what is smart card authentication