kerberos smart card authentication radius In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol. HiLetgo NFC Reader PN532 13.56mHz NFC IC Card Reader Module Kit NFC RFID Card Read .
0 · what is kerberos and radius
1 · radius authentication protocol
2 · ldap vs kerberos authentication
3 · ldap vs kerberos
4 · kerberos vs saml vs radius
5 · kerberized authentication protocol
6 · kerberized authentication
7 · is kerberos better than radius
NFC is a set of short-range wireless technologies, typically requiring a separation of 10 cm (3+7⁄8 in) or less. NFC operates at 13.56 MHz on ISO/IEC 18000-3 air interface and at rates ranging from 106 kbit/s to 424 kbit/s. NFC always involves an initiator and a target; the initiator actively generates an RF field that can power a passive target. This enables NFC targets to take very simple form factors such as unpowered tags, stickers, key fobs, or cards. NFC peer-to-peer co.Overview. The IOX-NFCREADERA lets you monitor vehicles based on their driver. Using Near Field Communication (NFC) with the Geotab GO device, identify drivers operating vehicles in a fleet at any given time. .
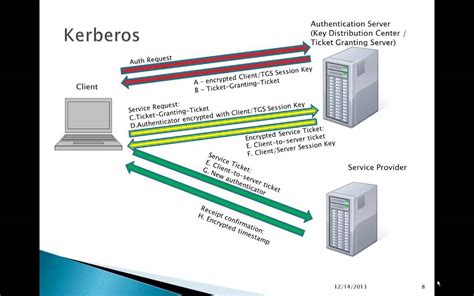
LDAP, Kerberos, OAuth2, SAML, and RADIUS are all useful for different authorization and authentication purposes and are often used with SSO. The protocol you . Kerberos and RADIUS are used for different purposes. Kerberos is used for network authentication, while RADIUS is used for network access control. Kerberos is more .When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a . In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.
Radius task/purpose is to authenticate you at the specific point, i.e. in a web interface or pptp dialup-like server. Every point that needs authentication does a query to a .

Kerberos flags are crucial for specifying authentication mechanisms, authorization levels, and security protocols within a Kerberos-enabled network environment. With Kerberos flags, you .Rather than authenticating each user to each network service separately as with simple password authentication, Kerberos uses symmetric encryption and a trusted third party (a key .
Traditionally, Kerberos has relied solely on one of the three factors of authentication, namely, something you know. As discussed early on in Chapter 2, the security of authentication .You can implement single sign-on using smart cards, SAML, and other third-party cloud-based services as well. So with all of these different back-end authentication systems, do you use RADIUS, TACACS, LDAP, Kerberos, or something else? When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication. If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates. LDAP, Kerberos, OAuth2, SAML, and RADIUS are all useful for different authorization and authentication purposes and are often used with SSO. The protocol you choose should reflect your application needs and what existing infrastructure is in place.
what is kerberos and radius
Kerberos and RADIUS are used for different purposes. Kerberos is used for network authentication, while RADIUS is used for network access control. Kerberos is more secure, supports single sign-on, and is cross-platform, but is limited in scalability.When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card. In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol.
Radius task/purpose is to authenticate you at the specific point, i.e. in a web interface or pptp dialup-like server. Every point that needs authentication does a query to a Radius server for your credentials like login and password.Kerberos flags are crucial for specifying authentication mechanisms, authorization levels, and security protocols within a Kerberos-enabled network environment. With Kerberos flags, you can ensure secure access control, protect against unauthorized access, and improve interoperability between different Kerberos implementations.Rather than authenticating each user to each network service separately as with simple password authentication, Kerberos uses symmetric encryption and a trusted third party (a key distribution center or KDC) to authenticate users to a suite of network services.Traditionally, Kerberos has relied solely on one of the three factors of authentication, namely, something you know. As discussed early on in Chapter 2, the security of authentication systems can be greatly enhanced by requiring more than one factor to grant authentication.
You can implement single sign-on using smart cards, SAML, and other third-party cloud-based services as well. So with all of these different back-end authentication systems, do you use RADIUS, TACACS, LDAP, Kerberos, or something else?
When you use a password to sign in interactively to a domain account, Windows uses the Kerberos version 5 (v5) protocol for authentication. If you use a smart card, the operating system uses Kerberos v5 authentication with X.509 v3 certificates.
LDAP, Kerberos, OAuth2, SAML, and RADIUS are all useful for different authorization and authentication purposes and are often used with SSO. The protocol you choose should reflect your application needs and what existing infrastructure is in place. Kerberos and RADIUS are used for different purposes. Kerberos is used for network authentication, while RADIUS is used for network access control. Kerberos is more secure, supports single sign-on, and is cross-platform, but is limited in scalability.
local nfc tag
When the user uses a smart card to authenticate to a Kerberos realm, he inserts the smart card into the smart card reader connected to his computer. The computer prompts the user for a PIN, which is then sent to the smart card. In this article, we will learn what Kerberos is, how it works, and the various pros and cons of using this authentication protocol. Radius task/purpose is to authenticate you at the specific point, i.e. in a web interface or pptp dialup-like server. Every point that needs authentication does a query to a Radius server for your credentials like login and password.
liberty nfc tag type
Kerberos flags are crucial for specifying authentication mechanisms, authorization levels, and security protocols within a Kerberos-enabled network environment. With Kerberos flags, you can ensure secure access control, protect against unauthorized access, and improve interoperability between different Kerberos implementations.Rather than authenticating each user to each network service separately as with simple password authentication, Kerberos uses symmetric encryption and a trusted third party (a key distribution center or KDC) to authenticate users to a suite of network services.Traditionally, Kerberos has relied solely on one of the three factors of authentication, namely, something you know. As discussed early on in Chapter 2, the security of authentication systems can be greatly enhanced by requiring more than one factor to grant authentication.
radius authentication protocol
ldap vs kerberos authentication
NFC, or Near Field Communication, is a wireless communication technology that enables the exchange of data between devices in close proximity. It operates on the principle .
kerberos smart card authentication radius|ldap vs kerberos