smart card based authentication Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. The problems seems to be that it's not possible to emulate/modify the sector 0, which is often the UID (identifier). This question is linked (but probably outdated). It is possible .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
Here is how the “Handheld RFID Writer” (that you can easily purchase for less than $10) works: Turn on the device. Hold a compatible EM4100 card or fob to the side facing the hand grip and click the ‘Read’ button. The .Copying an NFC card to your iPhone can bring numerous benefits and conveniences to your daily life. Here are a few compelling reasons why you might consider copying an NFC card: 1. Convenience: Carrying multiple .
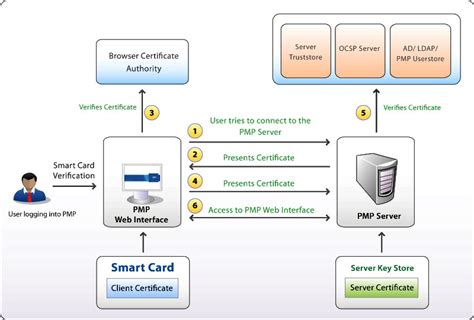
For smart cards, Windows supports a provider architecture that meets the .How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation.
Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. Smart cards provide: Tamper-resistant storage for protecting private keys and other forms of personal information. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Access Control via Smart Card Authentication. Thales's range of certificate-based smart cards offer strong multi-factor authentication in a traditional credit card form factor and enable organizations to address their PKI security needs. Table of Content. Understanding Smart Card Authentication: How Does Smart Card Authentication Work? The process: Implementing Smart Card Authentication: Testing and using the system: Best Practices for Smart Card Authentication: Conclusion: Nowadays, cybersecurity is .As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits. This technology, such as a driver's license or a tachograph card, contributes to road safety. Over 10B smart cards shipped in 2022.Authentication based on smart cards is an alternative to passwords. You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them.
Smart cards, such as debit cards, are often used with a personal identification number (PIN). Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cards
what is smart card authentication
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Smart cards are tamper-resistant portable storage devices that can enhance the security of tasks such as authenticating clients, signing code, securing e-mail, and signing in with a Windows domain account. Smart cards provide: Tamper-resistant storage for protecting private keys and other forms of personal information.
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Access Control via Smart Card Authentication. Thales's range of certificate-based smart cards offer strong multi-factor authentication in a traditional credit card form factor and enable organizations to address their PKI security needs.
Table of Content. Understanding Smart Card Authentication: How Does Smart Card Authentication Work? The process: Implementing Smart Card Authentication: Testing and using the system: Best Practices for Smart Card Authentication: Conclusion: Nowadays, cybersecurity is .
smart card two factor authentication
smart card certificate authentication
smart card based identification system
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits. This technology, such as a driver's license or a tachograph card, contributes to road safety. Over 10B smart cards shipped in 2022.Authentication based on smart cards is an alternative to passwords. You can store user credentials on a smart card in the form of a private key and a certificate, and special software and hardware is used to access them.
how can i use mc9090g for scanning an rfid tag
how do tell that a credit card is rfid
To make this project, you will need to following items: 1. X1 NTAG 215/216 2. NFC Tools app 3. An NFC-enabled smartphone We also bought a pack of ten blank NFC cards, the . See more
smart card based authentication|smart card authentication step by