eap authentication security solutions smart cards and biometrics EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption. Community for Animal Crossing New Horizons on the Nintendo Switch. Post about anything and everything related to New Horizons from your island, .
0 · windows eap authentication protocol
1 · extensible authentication protocol eap
2 · eap network security
3 · eap method for authentication
4 · eap fast server authentication
5 · eap fast authentication protocol
6 · eap authentication windows 10
7 · eap authentication protocol examples
Arduino Nano - RFID. This tutorial instructs you how to use RFID/NFC with Arduino Nano. The RFID/NFC system consists of two components: a reader and a tag. Two of the most popular RFID/NFC readers are the RC522 and PN532. .Could there be a way to scan amiibos without buying an nfc reader on o3ds models via cfw and a smartphone with nfc . . See if there's some CFW out there that can read Amiibo tags from a file using a custom key interrupt trigger. Once you have games talking to your Amiibo file, you can .
Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily .EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication methods, including as token .
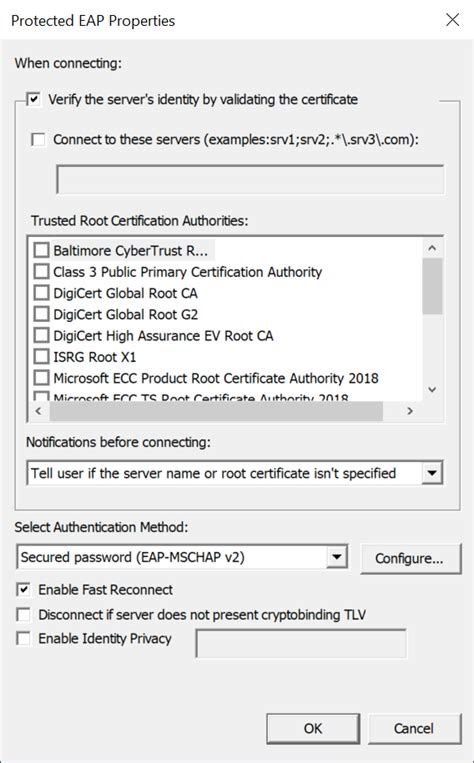
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS with certificates for mutual authentication. Appears .
Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily used in network communications.EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption.
This flexibility enables EAP to support different authentication mechanisms, such as passwords, digital certificates, smart cards, token-based authentication, biometrics, and more. The EAP framework consists of three main components: the EAP peer, the . Unlike proximity cards, smart cards using MIFARE DESFire EV1 technology offer several different layers of security, including mutual authentication, which ensures that the reader and the card.
windows eap authentication protocol
EAP is often used in cybersecurity and antivirus solutions to ensure that only authorized users can access sensitive data or systems. EAP enables mutual authentication between the client and server, which ensures that both parties can verify that the other is who they claim to be.
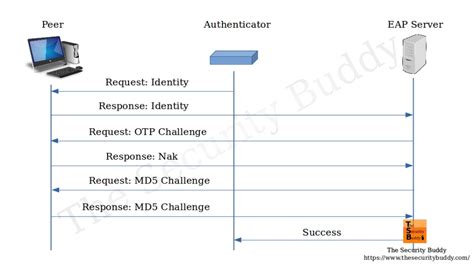
The Extensible Authentication Protocol (EAP) supports a variety of authentication methods, each designed to meet specific security requirements and operational contexts. Among the most significant are EAP-TLS, EAP-TTLS, PEAP, EAP-SIM, and EAP-AKA.The EAP-TLS authentication flow involves a secure exchange of certificates between the user's device and the authentication server, ensuring a trusted connection. Compared to other EAP methods, EAP-TLS provides faster and more secure authentication, making it .
An Extensible Authentication Protocol (EAP) is a Local Area Network (LAN) communication and point-to-point (P2P) wireless connecting framework. It helps authenticate clients, computers, or wireless LAN systems to the internet. With Extensible Authentication Protocol, networks can authenticate dial-up connections and LAN networks.
EAP-GTC, which stands for Extensible Authentication Protocol Generic Token Card, is a widely used protocol in cybersecurity landscapes to secure systems and protect them against cyber threats and unauthorized access.
extensible authentication protocol eap
This article contains configuration information specific to the following authentication methods in EAP. EAP-Transport Layer Security (EAP-TLS): Standards-based EAP method that uses TLS with certificates for mutual authentication. Appears .
Extensible Authentication Protocol (EAP) is a flexible framework supporting multiple authentication methods, such as passwords, smart cards, and digital certificates, primarily used in network communications.EAP is used on encrypted networks to provide a secure way to send identifying information to provide network authentication. It supports various authentication methods, including as token cards, smart cards, certificates, one-time passwords and public key encryption.
This flexibility enables EAP to support different authentication mechanisms, such as passwords, digital certificates, smart cards, token-based authentication, biometrics, and more. The EAP framework consists of three main components: the EAP peer, the . Unlike proximity cards, smart cards using MIFARE DESFire EV1 technology offer several different layers of security, including mutual authentication, which ensures that the reader and the card.
EAP is often used in cybersecurity and antivirus solutions to ensure that only authorized users can access sensitive data or systems. EAP enables mutual authentication between the client and server, which ensures that both parties can verify that the other is who they claim to be. The Extensible Authentication Protocol (EAP) supports a variety of authentication methods, each designed to meet specific security requirements and operational contexts. Among the most significant are EAP-TLS, EAP-TTLS, PEAP, EAP-SIM, and EAP-AKA.
The EAP-TLS authentication flow involves a secure exchange of certificates between the user's device and the authentication server, ensuring a trusted connection. Compared to other EAP methods, EAP-TLS provides faster and more secure authentication, making it . An Extensible Authentication Protocol (EAP) is a Local Area Network (LAN) communication and point-to-point (P2P) wireless connecting framework. It helps authenticate clients, computers, or wireless LAN systems to the internet. With Extensible Authentication Protocol, networks can authenticate dial-up connections and LAN networks.
eap network security

e.t.a by rosetti mykonos large crossbody bag with rfid-blocking pouch
lewis n clark wea rfid-blocking cross-body bag
Product Description. The ACR1252U USB NFC Reader III is an NFC Forum-certified PC-linked reader, developed based on 13.56Mhz contactless .SDK. ACR1255U-J1 ACS Secure Bluetooth® NFC Reader is designed to facilitate on-the-go smart card and NFC applications. It combines the latest 13.56 MHz contactless technology with Bluetooth® connectivity. ACR1255U-J1 supports .
eap authentication security solutions smart cards and biometrics|eap fast server authentication