how to write credentials to smart card How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. The 2022 NFL Playoff Schedule kicked off on Saturday, Jan. 14, 2023 with two Wild-Card games. In Super Bowl LVII, the Kansas City Chiefs defeated the Philadelphia Eagles 38-35 at State Farm .
0 · what is smart card authentication
1 · smart card identity
2 · smart card credential provider
3 · smart card based identification system
4 · smart card based authentication
5 · smart card authentication step by
6 · enable smart card authentication
7 · authenticate using your smart card
NFC card is a technology with huge possibilities. We've helped companies to use their cards for all purposes, from business name cards to retail store O2O interface, and even VIP gifts and branded souvenirs. Reach out to us to find .
rfid uhf handheld
what is smart card authentication
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. This document is intended for: Enterprise IT developers, managers, and staff who are planning to deploy or are using smart cards in their organization. Smart card vendors who . Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 .
smart card identity
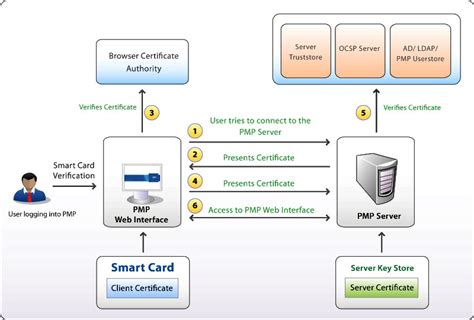
The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to .
In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a .Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS .
Authentication and signature keys are usually generated on the card and are not extractable, unlike encryption keys which can/should be escrowed somewhere. See Need help .These are "programmed", typically by using that storage and the API to install one or more certificates that are then used to identify the person using the card (usually in combination with .
6. In my organization, users must use SmartCard for interactive login to a Windows stations (95,Vista and 7). almost daily, we need to read the credentials stored in the .The following sections in this article describe how Windows uses the smart card architecture to select the correct smart card reader software, provider, and credentials for a successful smart card sign-in:How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system. This document is intended for: Enterprise IT developers, managers, and staff who are planning to deploy or are using smart cards in their organization. Smart card vendors who write smart card minidrivers or credential providers.
Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 security key such as the Yubikey 5 NFC. The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are. In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a .
Authentication and signature keys are usually generated on the card and are not extractable, unlike encryption keys which can/should be escrowed somewhere. See Need help using M2Crypto.Engine to access USB Token for an example with M2Crypto that explains how to use a smart card via PKCS#11 for website access in python. These are "programmed", typically by using that storage and the API to install one or more certificates that are then used to identify the person using the card (usually in combination with a PIN or biometric to "unlock" the card). 6. In my organization, users must use SmartCard for interactive login to a Windows stations (95,Vista and 7). almost daily, we need to read the credentials stored in the SmartCard and compaire them with the ActiveDirectory, without implementing a custom credentials manager. The fields we compare are: userPrincialName and sAMAccountName.The following sections in this article describe how Windows uses the smart card architecture to select the correct smart card reader software, provider, and credentials for a successful smart card sign-in:
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
This document is intended for: Enterprise IT developers, managers, and staff who are planning to deploy or are using smart cards in their organization. Smart card vendors who write smart card minidrivers or credential providers. Here’s a quick and easy way to generate a certificate for client authentication and smartcard logon that can be used when testing for example a PIV (PKI) capable FIDO2 security key such as the Yubikey 5 NFC.
The process: The user puts the smart card into a card reader hooked up to the device or system they want to use. The card reader talks to the smart card, asking the user to enter a password or give fingerprints to prove who they are. In this article we have covered the basics of Certificate-Based Authentication (CBA) using a smart card or a YubiKey (as a smart card). We have learned that CBA uses a certificate describing the user and that this certificate bundles a public key.Smart Card Logon for SSH For network engineers, this guide will help you authenticate with your PIV/CAC credential and use SSH to access a remote Linux server from a Windows or macOS computer. For server administrators, this guide will help you configure a . Authentication and signature keys are usually generated on the card and are not extractable, unlike encryption keys which can/should be escrowed somewhere. See Need help using M2Crypto.Engine to access USB Token for an example with M2Crypto that explains how to use a smart card via PKCS#11 for website access in python.
These are "programmed", typically by using that storage and the API to install one or more certificates that are then used to identify the person using the card (usually in combination with a PIN or biometric to "unlock" the card).
smart card credential provider
smart card based identification system
http www.buyinvengorfid.com xc-rf850-uhf-rfid-development-kit
rfid tamper evident cable seal/hm-uhf-c
CardSession requires the presence of an NFC reader, which isn’t supported in Simulator, to perform an ISO 7816 card emulation session. You can test with the following configurations: Your iPhone is running iOS 18.2 or later; Your iPhone .
how to write credentials to smart card|smart card based authentication