credentials carried inside smart card Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how . The Secure Element chip, an NFC chip that contains data such as the Secure Element identifier (SEID) for secure transactions. This chip is commonly found in smartphones and other NFC devices. Near-field communication (NFC) is a set .
0 · what is smart card authentication
1 · smart card identity
2 · smart card credential provider
3 · smart card based identification system
4 · smart card based authentication
5 · smart card authentication step by
6 · enable smart card authentication
7 · authenticate using your smart card
Same issue here after updating to Release 0.94.1. Switch did not recognize Amiibo cards from ACNH. Initially, it was also not possible to emulate actual Amiibo cards. But through: NFC > Extra Actions > Unlock NTAG/Ultralight > Auth as Ameebo and then scanning a .Amiibo data are stored on the physical Amiibo as a .bin file..Bin file - raw data from physical .
what is smart card authentication
Vendors provide smart cards and smart card readers, and in many cases the vendors are different for the smart card and the smart card reader. Drivers for smart . See more
And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second . Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. It contains data that . Here’s a primer on proximity, smart card, smart phone credentials, readers and long-range solutions for campus access control.
advanced cards systems acr122u-a9
smart card identity
Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how .
Biometric templates are now able to be carried inside a NFC-enabled smartphone along with other digital ID credentials.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded .Converged Credentials, or multi-application smart cards, are built on card architecture designs that perform multiple tasks across various ecosystems and domains. Their construction .
The most popular types of prox cards include: Smart Cards: Smart cards offer an added layer of security by incorporating microchips that can store more information than prox .
For smart card sign-in, a user's credentials are contained on the smart card's security chip. A smart card reader lets the computer interact with the security chip on the smart card. When users sign in with a smart card, they enter a personal identification number (PIN) instead of . And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure. Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. It contains data that identifies the cardholder. Key parts include smart cards, card readers, and computers that check identities. Card readers connect cards to computers.
Here’s a primer on proximity, smart card, smart phone credentials, readers and long-range solutions for campus access control. Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how passwords, smart cards, and virtual smart cards can be used to reach authentication goals in . Biometric templates are now able to be carried inside a NFC-enabled smartphone along with other digital ID credentials.
acr122u gui
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. [1] . Many smart cards include a pattern of metal contacts to electrically connect to the internal chip.
Converged Credentials, or multi-application smart cards, are built on card architecture designs that perform multiple tasks across various ecosystems and domains. Their construction requires a thorough understanding of the issues facing security, utility, conflicts, and costs.
The most popular types of prox cards include: Smart Cards: Smart cards offer an added layer of security by incorporating microchips that can store more information than prox cards. These cards can be used not only for access control but also for secure transactions and data storage. Why These Credentials Matter.For smart card sign-in, a user's credentials are contained on the smart card's security chip. A smart card reader lets the computer interact with the security chip on the smart card. When users sign in with a smart card, they enter a personal identification number (PIN) instead of . And while the ISO 7816 form-factor is steadily losing ground (evident by the lack of integrated readers in modern laptops), smart card authentication is experiencing a second coming, a revival brought on by recent mobile and cloud support in Microsoft Azure. Smart Card Authentication is how identity is checked using a smart card. The smart card has a microchip that can securely store and work with information. It contains data that identifies the cardholder. Key parts include smart cards, card readers, and computers that check identities. Card readers connect cards to computers.
Here’s a primer on proximity, smart card, smart phone credentials, readers and long-range solutions for campus access control. Comparing virtual smart cards with physical smart cards: compares properties, functional aspects, security, and cost. Authentication design options: describes how passwords, smart cards, and virtual smart cards can be used to reach authentication goals in .
Biometric templates are now able to be carried inside a NFC-enabled smartphone along with other digital ID credentials.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.A smart card (SC), chip card, or integrated circuit card (ICC or IC card), is a card used to control access to a resource. It is typically a plastic credit card-sized card with an embedded integrated circuit (IC) chip. [1] . Many smart cards include a pattern of metal contacts to electrically connect to the internal chip.
Converged Credentials, or multi-application smart cards, are built on card architecture designs that perform multiple tasks across various ecosystems and domains. Their construction requires a thorough understanding of the issues facing security, utility, conflicts, and costs.
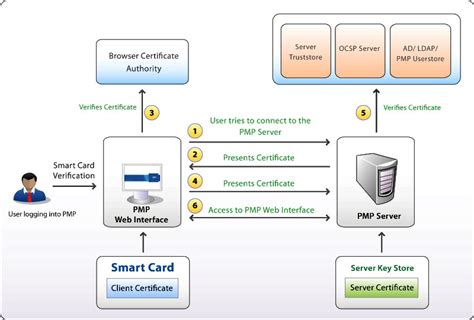
smart card credential provider

Professional Series USB Card/Tag Enroller ACENR-2C . 13.56MHz NFC Thin Proximity Cards .
credentials carried inside smart card|what is smart card authentication