how to a virus on nfc tag Some hackers can carry out an ATM hack through NFC if they wave a phone through certain contactless ATMs to make them disperse money. The technique is called a "jackpotting hack." Jackpotting is usually done by accessing . 1. Write function does not require root phone. 2. The write function needs to buy a special white card. 3. After writing a white card, the white card becomes your access card, and .
0 · what does nfc tag mean
1 · nfc tags on cell phone
2 · nfc tags not working
3 · nfc tags mobile
4 · nfc tag detected meaning
5 · nfc detected
6 · nfc card detected
7 · drive by nfc virus
In 2020, the NFL playoffs saw big changes to the postseason format as the league expanded its playoff bracket from a 12-team to a 14-team tournament. A third wild card team was also added for each .Find out which teams are winning the 2024 playoff race. Check out the NFL Playoff Picture for the latest team performance stats and playoff eliminations. Learn more.
Some hackers can carry out an ATM hack through NFC if they wave a phone through certain contactless ATMs to make them disperse money. The technique is called a "jackpotting hack." Jackpotting is usually done by accessing . When you scan an NFC tag containing a malware payload using your NFC-supported device, the malware is automatically downloaded and installed without your knowledge. Malware on your device can steal personal, financial, and login information, and can install malicious apps into your device.
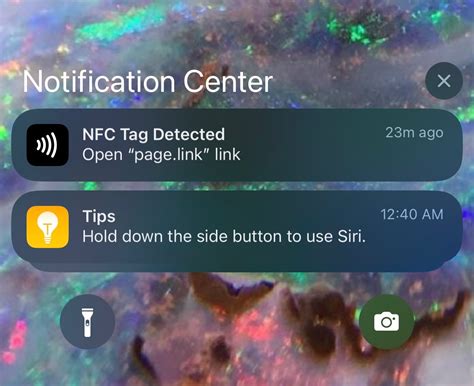
I am curious what security concerns come in to play with NFC tags and how to defend against these threats. For example, some tags could be reprogrammed without the user's knowledge or a tag may be cloned. Are there available methods for protecting integrity and confidentiality? This wikiHow article teaches you what it means when you see the notification, if it's trustworthy, and how to respond. Your phone will show an "NFC Tag Detected" if it detects a nearby AirTag, credit or debit card, NFC advertisement, or App Clip. The technology allows users to effortlessly transfer money, share files and knock out a growing list of other tasks. But that data transfer can create vulnerabilities. BBB has tips on what NFCs. Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at.
what does nfc tag mean
An NFC security key is of little use to a hacker if it only works in conjunction with a password or a biometric fingerprint scan. Likewise, a stolen NFC-enabled bank card won’t do a thief much good if they need access to a password-protected app on . A compromised NFC tag or device could be used to deliver malware to an unsuspecting user’s device. If a user’s device is set to read NFC tags automatically, the device could be infected simply by getting too close to a malicious tag.This article delves into the vulnerabilities of NFC technology, explores the evolution of NFC attacks, discusses the impact on individuals and businesses, and provides proactive measures and advanced protection strategies to safeguard your devices.
eastern conference standings nfl
The app is NGate, the malware that can capture NFC data from payment cards close to the infected device, and then send it to the attackers, either directly, or via a proxy. It does so. Some hackers can carry out an ATM hack through NFC if they wave a phone through certain contactless ATMs to make them disperse money. The technique is called a "jackpotting hack." Jackpotting is usually done by accessing . When you scan an NFC tag containing a malware payload using your NFC-supported device, the malware is automatically downloaded and installed without your knowledge. Malware on your device can steal personal, financial, and login information, and can install malicious apps into your device.I am curious what security concerns come in to play with NFC tags and how to defend against these threats. For example, some tags could be reprogrammed without the user's knowledge or a tag may be cloned. Are there available methods for protecting integrity and confidentiality?
nfc tags on cell phone
This wikiHow article teaches you what it means when you see the notification, if it's trustworthy, and how to respond. Your phone will show an "NFC Tag Detected" if it detects a nearby AirTag, credit or debit card, NFC advertisement, or App Clip. The technology allows users to effortlessly transfer money, share files and knock out a growing list of other tasks. But that data transfer can create vulnerabilities. BBB has tips on what NFCs. Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at.
An NFC security key is of little use to a hacker if it only works in conjunction with a password or a biometric fingerprint scan. Likewise, a stolen NFC-enabled bank card won’t do a thief much good if they need access to a password-protected app on . A compromised NFC tag or device could be used to deliver malware to an unsuspecting user’s device. If a user’s device is set to read NFC tags automatically, the device could be infected simply by getting too close to a malicious tag.
This article delves into the vulnerabilities of NFC technology, explores the evolution of NFC attacks, discusses the impact on individuals and businesses, and provides proactive measures and advanced protection strategies to safeguard your devices.
new england patriots nfl standings
nfc tags not working
wild card rankings
miami dolphins standings playoffs
lokogan28. •. Most reliable option is NFC Card Emulator Pro by Yuanwofei. App is available on play store. Limited compatibility. Check info to see if your phone and card are compatible. Reply. PlumCurious6273. •.
how to a virus on nfc tag|nfc tags not working