nfc security tags The NFC authentication process explained. There are variants of the NFC tag authentication process but the principle is similar. Each tag is encoded with a special key that cannot be seen. That key is used to generate a unique code on each scan which can be added to the standard NDEF data. Discover ST's solutions for NFC / RFID applications, including tags and readers, dynamic tags, NFC controllers and secure elements supported by a rich development ecosystem.
0 · what is website nfc tag
1 · what is nfc tag means
2 · types of nfc tags
3 · nfc tracking tags
4 · nfc tags where to buy
5 · nfc tags for apple phones
6 · nfc tags explained
7 · nfc tag definition
The Square Reader (2nd Generations) lets you accept every way your customers want to pay: take bank cards, Apple Pay, and other NFC payments. You can also send invoices and key in bank card numbers by hand. The reader connects .

NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to . NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to the reader in the form of electromagnetic pulses. The NFC authentication process explained. There are variants of the NFC tag authentication process but the principle is similar. Each tag is encoded with a special key that cannot be seen. That key is used to generate a unique code on each scan which can be added to the standard NDEF data.
NFC security seals and labels are essential components of today’s supply chain. ☛ Learn how tags with blockchain prevents counterfeiting and fraud.Smart tags are tiny, read-only chips that can appear in informational posters and identification documents, such as corporate badges or passports. You can even use NFC to connect to secure networks without having to enter complex authorization codes. NFC tags are small, thin adhesive stickers or chips that can be attached to objects or embedded within them. These tags store and transmit data when they come into contact with an NFC-enabled device, such as a smartphone or tablet. The functionality of NFC tags is what makes them truly remarkable.
By intercepting the radio waves used for NFC communication, attackers can potentially gain unauthorized access to sensitive information or clone NFC tags, compromising the security of the communication process. Relying on physical access to a device to authenticate someone’s identity is risky, however, because it means that a person who steals an NFC tag or security key could gain unauthorized access to places and systems protected by the stolen device.
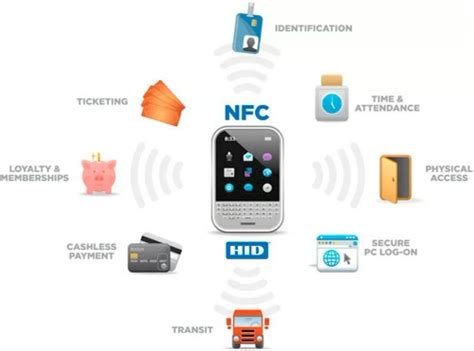
NFC technology allows for seamless and secure communication between NFC-enabled devices and tags through electromagnetic coupling. This enables tasks such as mobile payments, information sharing, access control, and smart home automation with a simple tap or wave of a device.NTAG 424 DNA solutions are highly secure and powerful NFC tags that are ideal for protecting assets and data while enabling advanced functionality. Features AES cryptography, SUN message authentication, a sensitive data storage protected by .Infineon's Secured NFC tags offer superior security performance based on robust cryptography for seamless authentication of products and accessories.
what is website nfc tag
NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data on them that is sent to the reader in the form of electromagnetic pulses. The NFC authentication process explained. There are variants of the NFC tag authentication process but the principle is similar. Each tag is encoded with a special key that cannot be seen. That key is used to generate a unique code on each scan which can be added to the standard NDEF data. NFC security seals and labels are essential components of today’s supply chain. ☛ Learn how tags with blockchain prevents counterfeiting and fraud.Smart tags are tiny, read-only chips that can appear in informational posters and identification documents, such as corporate badges or passports. You can even use NFC to connect to secure networks without having to enter complex authorization codes.
NFC tags are small, thin adhesive stickers or chips that can be attached to objects or embedded within them. These tags store and transmit data when they come into contact with an NFC-enabled device, such as a smartphone or tablet. The functionality of NFC tags is what makes them truly remarkable. By intercepting the radio waves used for NFC communication, attackers can potentially gain unauthorized access to sensitive information or clone NFC tags, compromising the security of the communication process.
Relying on physical access to a device to authenticate someone’s identity is risky, however, because it means that a person who steals an NFC tag or security key could gain unauthorized access to places and systems protected by the stolen device.
NFC technology allows for seamless and secure communication between NFC-enabled devices and tags through electromagnetic coupling. This enables tasks such as mobile payments, information sharing, access control, and smart home automation with a simple tap or wave of a device.NTAG 424 DNA solutions are highly secure and powerful NFC tags that are ideal for protecting assets and data while enabling advanced functionality. Features AES cryptography, SUN message authentication, a sensitive data storage protected by .
what is nfc tag means
testing rfid systems
vehicle tracking system using rfid ppt
Restored New Nintendo 2DS XL Video Game Console with NFC Amiibo Reader .
nfc security tags|nfc tags for apple phones