rfid tag point spoof There are a number of attacks associated with RFID technologies. One is a simple data capture. If you can sit in the middle of that wireless communication, you can view what’s going back and forth between the RFID tag. Another thing you could do is to even spoof the reader. $34.96
0 · what is rfid spoofing
1 · rfid spoofer
The wild card club with the best record; The wild card club with the second-best record; The wild card club with the third-best record; The following procedures will be used to break standings ties for postseason playoffs and to determine .
By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack .There are a number of attacks associated with RFID technologies. One is a simple data capture. If you can sit in the middle of that wireless communication, you can view what’s going back and forth between the RFID tag. Another thing you could do is to even spoof the reader.
sisc health smarts award card
From there he built this tag spoofer with a keypad on which you enter the number from the back of any 125 kHz tag and the device becomes that tag. Cloning is duplicating data from a pre-existing tag, and spoofing is then using the cloned tag to gain access to a secured area or item. Because the hacker has to know the data . Arduino RFID Spoofer. An Arduino, a spent roll of toilet paper, magnet wire, and a few passive components are what’s needed to build this RFID spoofer. It’s quick, dirty, and .
Right now, the spoofer can only handle reading and spoofing 125kHz RFID tags with no encryption or authorization. A tag that’s more complex than the duct tape RFID tag .
smart 51s card printer driver
They’re used in building access control systems, passports, inventory tracking.. This instructable will show how you can use an Arduino and a few simple components (wire .Depending on what you get, cloning may be anything from from easy (just use tag info app) up to quite hard (you need to brute-force a key, disassemble a lock or read the tag contents using .RFID spoofing is a cybersecurity threat where attackers mimic the signals of legitimate RFID tags to deceive RFID readers. This technique allows unauthorized individuals to gain access to secure areas or systems by presenting false data as if it were genuine. By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.
site microsoft.com smart card logon windows 10 multiple factor
There are a number of attacks associated with RFID technologies. One is a simple data capture. If you can sit in the middle of that wireless communication, you can view what’s going back and forth between the RFID tag. Another thing you could do is to even spoof the reader.
From there he built this tag spoofer with a keypad on which you enter the number from the back of any 125 kHz tag and the device becomes that tag. Spoofing. By spoofing a valid RFID tag, an attacker could fool an automated checkout system into thinking that a product was still on the shelf. Or, an attacker might re-write or replace tags. Cloning is duplicating data from a pre-existing tag, and spoofing is then using the cloned tag to gain access to a secured area or item. Because the hacker has to know the data on the tag to clone it, this type of attack is mainly seen in access or asset management operations. Arduino RFID Spoofer. An Arduino, a spent roll of toilet paper, magnet wire, and a few passive components are what’s needed to build this RFID spoofer. It’s quick, dirty, and best of all.
Right now, the spoofer can only handle reading and spoofing 125kHz RFID tags with no encryption or authorization. A tag that’s more complex than the duct tape RFID tag doesn’t work.
They’re used in building access control systems, passports, inventory tracking.. This instructable will show how you can use an Arduino and a few simple components (wire coil, transistor, capacitor, resistor) to make a device that can spoof an .
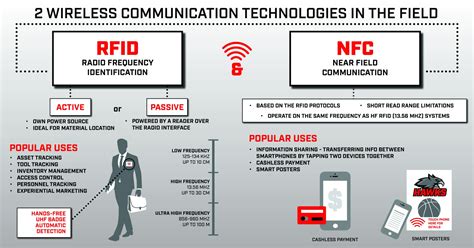
Depending on what you get, cloning may be anything from from easy (just use tag info app) up to quite hard (you need to brute-force a key, disassemble a lock or read the tag contents using proxmark and then use tag emulator to bypass auth).RFID spoofing is a cybersecurity threat where attackers mimic the signals of legitimate RFID tags to deceive RFID readers. This technique allows unauthorized individuals to gain access to secure areas or systems by presenting false data as if it were genuine.
what is rfid spoofing
rfid spoofer
By closely monitoring the power consumption levels of RFID tags, hackers can fool your systems. With some ingenuity and a cell phone bad actors can perform an RFID hack that will steal sensitive information or breach secured areas.There are a number of attacks associated with RFID technologies. One is a simple data capture. If you can sit in the middle of that wireless communication, you can view what’s going back and forth between the RFID tag. Another thing you could do is to even spoof the reader.
From there he built this tag spoofer with a keypad on which you enter the number from the back of any 125 kHz tag and the device becomes that tag.
Spoofing. By spoofing a valid RFID tag, an attacker could fool an automated checkout system into thinking that a product was still on the shelf. Or, an attacker might re-write or replace tags. Cloning is duplicating data from a pre-existing tag, and spoofing is then using the cloned tag to gain access to a secured area or item. Because the hacker has to know the data on the tag to clone it, this type of attack is mainly seen in access or asset management operations. Arduino RFID Spoofer. An Arduino, a spent roll of toilet paper, magnet wire, and a few passive components are what’s needed to build this RFID spoofer. It’s quick, dirty, and best of all.
Right now, the spoofer can only handle reading and spoofing 125kHz RFID tags with no encryption or authorization. A tag that’s more complex than the duct tape RFID tag doesn’t work.
They’re used in building access control systems, passports, inventory tracking.. This instructable will show how you can use an Arduino and a few simple components (wire coil, transistor, capacitor, resistor) to make a device that can spoof an .

smart access card entry in creta
sim card sim registration smart
Waving one's hand over an ill-placed sensor is all that's needed to get past a new set of $700,000 subway gates the MTA is testing to crack down on fare-beating, which was exposed in a TikTok video.So no, RFID readers can't read nfc tags and NFC readers can't read RFID tags. I'd suggest .
rfid tag point spoof|rfid spoofer