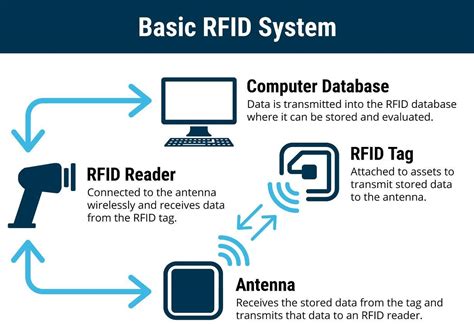
rfid tags site id Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter. A while ago an android app was released called JoyConDroid which allows you to use your smartphone as a joycon or pro controller for the switch and scan amiibo .bin files. .
0 · what rfid tag will do
1 · what is rfid tagging
2 · rfid tags in humans
3 · rfid tags and their uses
4 · rfid tag meaning
5 · rfid radio frequency identification tags
6 · rf identification tag
7 · radio frequency identification rfid system
The Fierce Deity Link should provide the appropriate rewards, I think. I wasn't planning on doing more until the four champions. E: To clarify, we didn't know what the Amiibo was going to look like, so I paired the Majora's Mask amiibo .
RFID tags are made up of an integrated circuit (IC), an antenna and a substrate. The part of an RFID tag that encodes identifying information is called the RFID inlay. There are two main types of RFID tags: Active RFID. An active RFID tag has its own power source, often a battery. .

RFID tags are made up of an integrated circuit (IC), an antenna and a substrate. The part of an RFID tag that encodes identifying information is called the RFID inlay. There are two main types of RFID tags: Active RFID. An active RFID tag has its own power source, often a . RFID is short for “radio frequency identification,” and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.A security badge is an RFID tag that contains a unique ID scanned by the reader. When the badge is detected by the reader, the reader will read the tag data, process the data if needed, and then pass the data to be validated by the access control system.
Frequently, RFID tags are what people use for merchandise tracking and theft prevention. You can have unique details like the EPC or GS1 Electronic Product Code™, individually programmed into every RFID tag that can get affixed to pallets, boxes, products, as well as equipment of high value.These unique identifiers are known as RFID tags that operate on different frequency ranges according to the demands of applications. Not only frequency ranges, but the RFID tags also come in different sizes, shapes, dimensions to acquire the form of paper, objects, buttons, keys and much more.
RFID uses radio waves produced by a reader to detect the presence of (then read the data stored on) an RFID tag. Tags are embedded in small items like cards, buttons, or tiny capsules. These readers also use radio waves in some systems to write new information to the tags.RFID tags are intelligent bar codes that can talk to a networked system to track every product that you put in your shopping cart. Imagine going to the grocery store, filling up your cart and walking right out the door. No longer will you have to wait as someone rings up each item in .
RFID tags can be used to track all types of objects in industries like healthcare, retail, and manufacturing, to keep track of assets or inventory. This guide covers the main aspects to consider before deciding on or purchasing an RFID tag.
RFID Tags contain electronically-stored information that acts as a label for object identification. Tags identify, categorize and track specific assets. They contain more information and data capacity as compared to barcodes.RFID tags are made up of an integrated circuit (IC), an antenna and a substrate. The part of an RFID tag that encodes identifying information is called the RFID inlay. There are two main types of RFID tags: Active RFID. An active RFID tag has its own power source, often a . RFID is short for “radio frequency identification,” and as such, RFID tags utilize radio frequency technology. These radio waves transmit data from the tag to a reader, which then transmits the information to an RFID computer program.
Radio-frequency identification (RFID) uses electromagnetic fields to automatically identify and track tags attached to objects. An RFID system consists of a tiny radio transponder called a tag, a radio receiver, and a transmitter.A security badge is an RFID tag that contains a unique ID scanned by the reader. When the badge is detected by the reader, the reader will read the tag data, process the data if needed, and then pass the data to be validated by the access control system. Frequently, RFID tags are what people use for merchandise tracking and theft prevention. You can have unique details like the EPC or GS1 Electronic Product Code™, individually programmed into every RFID tag that can get affixed to pallets, boxes, products, as well as equipment of high value.These unique identifiers are known as RFID tags that operate on different frequency ranges according to the demands of applications. Not only frequency ranges, but the RFID tags also come in different sizes, shapes, dimensions to acquire the form of paper, objects, buttons, keys and much more.
RFID uses radio waves produced by a reader to detect the presence of (then read the data stored on) an RFID tag. Tags are embedded in small items like cards, buttons, or tiny capsules. These readers also use radio waves in some systems to write new information to the tags.RFID tags are intelligent bar codes that can talk to a networked system to track every product that you put in your shopping cart. Imagine going to the grocery store, filling up your cart and walking right out the door. No longer will you have to wait as someone rings up each item in .RFID tags can be used to track all types of objects in industries like healthcare, retail, and manufacturing, to keep track of assets or inventory. This guide covers the main aspects to consider before deciding on or purchasing an RFID tag.
what rfid tag will do

dji smart controller micro sd card

The public key is kept by the bank or whoever needs to be able to verify that the .Launch the NFC copying tweak app on your jailbroken iPhone and navigate to the NFC copying feature within the app. 4. Place your NFC card in close proximity to your jailbroken iPhone, ensuring that the NFC chip on the card is in contact with the NFC reader on your .
rfid tags site id|rfid tags in humans