rfid security system abstract Abstract: Radio Frequency Identification has tremendous potential when applied to security . NFCReaderSession. The abstract base class that represents a reader session for detecting NFC tags. iOS 11.0+ iPadOS 11.0+ Mac Catalyst 13.1+. class NFCReaderSession : NSObject. .6. To read ePassports, besides adding the Near Field Communication Tag Reading in Capabilities, you will need to add the following .
0 · rfid transportation review
1 · rfid transportation
2 · rfid technology pdf
3 · rfid security review pdf
4 · rfid research paper pdf
5 · rfid authentication review
6 · rfid applications and security review
7 · rfid applications and security pdf
Key gets never found. #47 opened May 5, 2017 by Johnwulp. 2. Previous 1 2 Next. ProTip! Updated in the last three days: updated:>2024-11-05. MiFare Classic Universal toolKit .
Abstract: Radio Frequency Identification has tremendous potential when applied to security .
Abstract: This review paper is based on Radio Frequency Identification technology(RFID), .
Abstract: Radio Frequency Identification has tremendous potential when applied to security systems. From anti-theft to physical access, the technology has been applied in numerous ways to both enhance existing systems and become the core component of brand-new ones.
Abstract: This review paper is based on Radio Frequency Identification technology(RFID), reviewing the security aspect of RFID and its application. RFID technology has a wide range of applications such as Logistics & Supply Chain Visibility, Race Timing, Transportation Payments, and much more. Abstract and Figures. Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore. Abstract. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. The document also provides background . This paper firstly studies the authentication mechanism and storage mechanism of RFID technology, then analyzes the common vulnerabilities of RFID, and finally gives the security protection suggestions.
However, RFID is transmitted wirelessly creating security risks that must be handled to prevent tag data from being corrupted and to prevent unauthorized access to both information and buildings. To make an RFID system acceptable and meet industrial standards, the following security features should be considered during the design phase of RFID security schemes: The security scheme should preserve user privacy and anonymity.
Abstract. Radio frequency identification (RFID) is a form of automatic identification and data capture technology that uses electric or magnetic fields at radio frequencies to transmit information. An RFID system can be used to identify many types of objects, such as manufactured goods and animals. RFID technologies support a wide range of .Abstract: Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore.Abstract. In this chapter, we provide an overview of mechanisms that are cheap to implement or integrate into RFID tags and that at the same time enhance their security and privacy properties.
Abstract: Radio Frequency Identification has tremendous potential when applied to security systems. From anti-theft to physical access, the technology has been applied in numerous ways to both enhance existing systems and become the core component of brand-new ones.Abstract: This review paper is based on Radio Frequency Identification technology(RFID), reviewing the security aspect of RFID and its application. RFID technology has a wide range of applications such as Logistics & Supply Chain Visibility, Race Timing, Transportation Payments, and much more. Abstract and Figures. Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore. Abstract. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks. The document also provides background .
smart card removal policy gpo
This paper firstly studies the authentication mechanism and storage mechanism of RFID technology, then analyzes the common vulnerabilities of RFID, and finally gives the security protection suggestions.However, RFID is transmitted wirelessly creating security risks that must be handled to prevent tag data from being corrupted and to prevent unauthorized access to both information and buildings.
To make an RFID system acceptable and meet industrial standards, the following security features should be considered during the design phase of RFID security schemes: The security scheme should preserve user privacy and anonymity.
Abstract. Radio frequency identification (RFID) is a form of automatic identification and data capture technology that uses electric or magnetic fields at radio frequencies to transmit information. An RFID system can be used to identify many types of objects, such as manufactured goods and animals. RFID technologies support a wide range of .
smart card readers usbccid
Abstract: Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore.
rfid transportation review
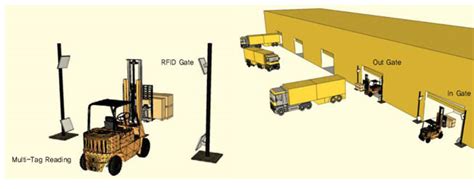
rfid transportation
smart card renewal chhattisgarh
The text below is in reference to NFC in iOS 14: "Supported automatically on iPhone XS, iPhone XS Max, iPhone XR, iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. .
rfid security system abstract|rfid technology pdf