smart card technology authentication for personal identification According to the 11 February 2023Eurosmartforecasts, smart card markets will probably exceed 10 billion units in 2022. The . See more Tiger Talk, Auburn's popular weekly radio show, returns on Thursday nights at 6 p.m. CT starting on August 24. . 2023 AUBURN FOOTBALL RADIO AFFILIATES. City .
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Listen to college football plus every NFL, MLB, and NHL game. Catch all the sports, music, news, podcasts, and talk you want on TuneIn.
It integrates a microprocessor, some memory, and some apps. The circular metal contact is vital to connect to the chip below and activate the card electrically. It's used with a contact or contactless card reader(POS for payments, at the ATM, or even on your mobile phone). Why? The card reader (or mobile phone) . See moreIn the form of credit cards and SIM cards, smart cardsare the most common form of IT processing power on the planet. It is estimated that . See more
According to Markets and Markets' recent research report, the smart card marketvalueis expected to reach .9 billion by 2026. . See moreAccording to the 11 February 2023Eurosmartforecasts, smart card markets will probably exceed 10 billion units in 2022. The . See moreRoland Moreno patented the memory card in 1974. By 1977, three commercial manufacturers, Bull CP8, SGS Thomson, and Schlumberger, started developing smart card products. In March 1979, Michel Hugon from Bull CP8 was the first to design and . See moreAuthentication. Smart card technology provides mechanisms for authenticating others who want to gain access to the card or device. These mechanisms can be used to authenticate users, devices, or applications wishing to use the data on .
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits.
Authentication. Smart card technology provides mechanisms for authenticating others who want to gain access to the card or device. These mechanisms can be used to authenticate users, devices, or applications wishing to use the data on the card’s or device’s chip.Smart Cards and Identity Applications. Smart card technology is currently recognized as the most appropriate technology for identity applications that must meet critical security requirements, including: Authenticating the bearer of an identity credential when used in conjunction with personal identification numbers (PINs) or biometric .
Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Smart cards are often used for personal identification numbers, authentication, data storage, and other applications like secure transactions. They can communicate with readers through direct physical contact or remote connections using .Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the user's authentication credentials, such as a personal identification number (PIN), digital certificates, and biometric data.
Smart Cards for Authentication. NIST started its work on smart cards in the late 1980s. Researchers at the agency wanted to expand work being done at the Department of the Treasury, which initially focused on putting standard cryptographic algorithms on smart cards for authentication purposes.Smart cards have significantly improved security in financial transactions and personal identification. They provide a secure and convenient way to access services and information, making them essential in modern society.
Privacy and Secure Identification Systems: The Role of Smart Cards as a Privacy-Enabling Technology. A Smart Card Alliance White Paper. February 2003. Smart Card Alliance. 191 Clarksville Rd. Princeton Junction, NJ 08550. www.smartcardalliance.org. Telephone: 1-800-556-6828. Table of Contents ____________________________________________ 2.As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits.
Authentication. Smart card technology provides mechanisms for authenticating others who want to gain access to the card or device. These mechanisms can be used to authenticate users, devices, or applications wishing to use the data on the card’s or device’s chip.Smart Cards and Identity Applications. Smart card technology is currently recognized as the most appropriate technology for identity applications that must meet critical security requirements, including: Authenticating the bearer of an identity credential when used in conjunction with personal identification numbers (PINs) or biometric . Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Smart cards provide an easy and movable way to prove who you are, without needing to remember hard passwords. Smart card security can be combined with other authentication methods like personal identification numbers or biometrics for stronger protection. Implementing Smart Card Authentication:
Smart cards are often used for personal identification numbers, authentication, data storage, and other applications like secure transactions. They can communicate with readers through direct physical contact or remote connections using .Smart card authentication is a security technology that uses smart cards, which are small plastic cards with embedded microchips, to prove a user's identity. The microchip securely stores the user's authentication credentials, such as a personal identification number (PIN), digital certificates, and biometric data.
Smart Cards for Authentication. NIST started its work on smart cards in the late 1980s. Researchers at the agency wanted to expand work being done at the Department of the Treasury, which initially focused on putting standard cryptographic algorithms on smart cards for authentication purposes.Smart cards have significantly improved security in financial transactions and personal identification. They provide a secure and convenient way to access services and information, making them essential in modern society.
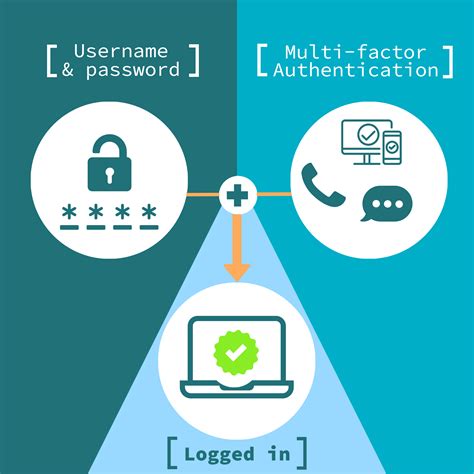
smart card multi factor authentication
smart card identity
TIGER TALK. Thursdays at 6 p.m. CT. Hosted by Brad Law and the Voice of .
smart card technology authentication for personal identification|smart card based identification system