stealing contactless card details A security flaw could allow thieves to steal information from contactless payments cards of millions of people, allowing them to buy items costing thousands of pounds. When you interact with our mobile applications or online services, we and .
0 · theft of contactless payments
1 · how to steal debit cards
2 · how to steal credit card details
3 · how to steal a credit card number
4 · contactless payment card stolen
5 · contactless payment card limit uk
6 · contactless card theft
7 · can anyone steal credit card information
NFC-F and NFC-A/B are similar at the very basic of protocols, but over-all are two very .NFCTools is a collection of libraries and tools for NFC in Java. The targeted devices are desktop Reader/Writer and Android smart phones. Most functions in the library have been .
theft of contactless payments
printing of dl in form 7 smart card pending
how to steal debit cards
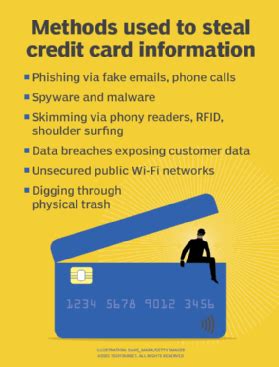
Cybercriminals often trick people into entering their credit card details on fake websites by sending phishing links via email or text (sometimes referred to as *smishing*). . A security flaw could allow thieves to steal information from contactless payments cards of millions of people, allowing them to buy items costing thousands of pounds. Cybercriminals often trick people into entering their credit card details on fake websites by sending phishing links via email or text (sometimes referred to as *smishing*). .
A security flaw could allow thieves to steal information from contactless payments cards of millions of people, allowing them to buy items costing thousands of pounds. 6. RFID collection (i.e., intercepting contactless payment) Many modern cards use radio-frequency identification (RFID) for contactless payment. A thief close enough to you with . If someone asks you to provide your card details over the phone on behalf of the card Issuer, do not agree. Call the customer support number on the back of your card and ask .

Fraudsters would use long-range RFID readers to extract data from contactless cards from a distance and use that card data to access cardholders' accounts and steal money. Criminals install card skimming devices on ATMs and card terminals to steal cards’ information. You can protect yourself by paying with a contactless card, digital wallet or .
public affairs army smart card
The app is NGate, the malware that can capture NFC data from payment cards close to the infected device, and then send it to the attackers, either directly, or via a proxy. Fraudsters may send fake, official-looking emails from banks or large retail stores asking you to click a link or call a phone number and give out personal information like account . Any lost or stolen card can be used for fraud, regardless if it has contactless capabilities or not. Mobile payment apps may also be used for fraudulent purchases, assuming . Card skimming occurs when thieves install hidden devices on payment terminals to steal your credit or debit card information. These skimmers are often placed on ATMs, gas .

Cybercriminals often trick people into entering their credit card details on fake websites by sending phishing links via email or text (sometimes referred to as *smishing*). . A security flaw could allow thieves to steal information from contactless payments cards of millions of people, allowing them to buy items costing thousands of pounds. 6. RFID collection (i.e., intercepting contactless payment) Many modern cards use radio-frequency identification (RFID) for contactless payment. A thief close enough to you with .
If someone asks you to provide your card details over the phone on behalf of the card Issuer, do not agree. Call the customer support number on the back of your card and ask .
Fraudsters would use long-range RFID readers to extract data from contactless cards from a distance and use that card data to access cardholders' accounts and steal money.
Criminals install card skimming devices on ATMs and card terminals to steal cards’ information. You can protect yourself by paying with a contactless card, digital wallet or .
The app is NGate, the malware that can capture NFC data from payment cards close to the infected device, and then send it to the attackers, either directly, or via a proxy.
Fraudsters may send fake, official-looking emails from banks or large retail stores asking you to click a link or call a phone number and give out personal information like account . Any lost or stolen card can be used for fraud, regardless if it has contactless capabilities or not. Mobile payment apps may also be used for fraudulent purchases, assuming .
Here are some of my favorite creative ways to use NFC tags with your iPhone. 1. Instantly connect to a Wi-Fi network. One of the biggest pains of living in the digital age is remembering complicated passwords. NFC can .
stealing contactless card details|contactless payment card stolen